Understanding PCI Compliance
Small businesses that accept credit card payments are required to protect customers’ payment card information under card network agreements. Not only this, but when a customer hands over a card at a cafe, online shop or service desk they trust the business to keep the number, expiry date and security code safe. The Payment Card Industry Data Security Standard (PCI DSS) is a set of requirements designed to help businesses know how to keep cardholder information secure. It was created by the major card brands through the PCI Security Standards Council and applies to any business that stores, processes or transmits card details. Compliance is not a law but card brands enforce it through contracts and fines for noncompliance. This article explains what the PCI requires and gives practical steps to help small businesses maintain compliance when accepting card payments.
Overview of the PCI DSS Requirements
The PCI standard contains twelve main requirements. The objective of the requirements is to cover network security, protection of cardholder data, vulnerability management, access control, monitoring and testing, and supporting policies.
Breaking Down the Twelve Requirements
The twelve requirements of PCI DSS version 4.0 provide concrete actions. You may not need to implement every control if you use a payment processor that stores and tokenizes card data on your behalf. However, understanding the requirements will help you decide which tasks you will need to complete.
1. Install and Maintain Network Security Controls
A firewall creates a barrier between trusted and untrusted networks. It controls incoming and outgoing traffic and blocks unauthorized access. A small business can meet this requirement by using a router with firewall features, segmenting Wi-Fi for guests and employees, and closing unused ports on all devices. Cloud based point of sale systems, like those used with tablets, still depend on local networks to connect to the internet, so modern routers with secure configurations are essential to keep hackers from intercepting transaction data over your Wi-Fi connection. Avoid default passwords on routers and change them to strong passphrases that are not easily guessed, such as your business street address. Review firewall rules periodically to ensure they only permit necessary traffic.
2. Apply Secure Configurations to All Systems
Most consumer software systems and devices come with default settings that prioritize ease of use rather than security. Examples include generic administrator accounts and starter passwords. Secure configuration means hardening systems by disabling unneeded services, removing vendor supplied accounts, and applying configuration templates that follow best practices. For a small business this could include turning off remote management on card terminals, disabling Bluetooth and other wireless features that are not required, and ensuring that payment applications can only be access with administrator user accounts. Document these configurations so that they can be applied consistently when devices are replaced or updated.
3. Protect Stored Cardholder Data
The best way to protect stored cardholder data is to avoid storing it altogether. Many small businesses use payment gateways or processing services that handle storage and tokenization, which removes sensitive data from your own systems. If storage at your business or within your own systems is unavoidable, it must be done within PCI standards. Failing to store customer payment data securely can result if its theft, which can result in hefty penalties and lawsuits. Often, small businesses that face such data breaches do not survived the financial fallout that follows.
4. Protect Cardholder Data During Transmission
Data is most at risk when it travels across networks. When a customer enters card information through a website or a payment terminal sends transaction details to a processor, that data must be encrypted. Use secure protocols such as Transport Layer Security (TLS) for web pages and secure wireless networks with strong encryption like WPA three. If a business uses a virtual terminal for phone orders, ensure that the browser connection is secure and that the device is free from malware. Never send card information through email or instant messages as it can be easily intercepted by hackers. If details must be shared within your organization, use secure portals designed for sending sensitive files and data. Some processors even offer such systems outside of there processing gateways.
5. Protect Systems and Networks from Malware
Malware and viruses can infect computers, tablets and even point of sale terminals. Use reputable anti-malware software and enable real-time scanning to detect and block malicious files. Keep the software updated along with the operating system and other applications so that known vulnerabilities are patched. Train staff not to open suspicious attachments or click unknown links. If your business uses mobile devices for orders, install only approved applications from trusted sources. A simple infection can capture card data through keylogging or screen scraping, so preventing malware is a critical part of compliance.
6. Develop and Maintain Secure Systems and Software
Every time a vendor releases an update for an operating system or application it often addresses security flaws. Apply patches promptly and monitor vendor announcements for critical updates. If your business uses a custom e-commerce site or develops its own software, follow secure coding practices and perform code reviews and third-party security audits. Use a staging environment to test updates before deploying them in production. Documentation should specify who is responsible for applying updates and how they are tracked. This requirement also applies to hardware devices such as payment terminals; ensure that firmware updates are applied according to vendor guidance.
7. Restrict Access Based on Business Need
Each person who accesses systems handling card data must be uniquely identified. Use unique usernames rather than shared accounts, and require strong passwords or passphrases. Multi-factor authentication adds an extra layer of protection by requiring something the user knows (a password) and something the user has (a token or code). Small businesses can implement multi-factor authentication through software tokens or authenticator apps. Avoid using generic login names like admin or manager. If remote access is required, such as when accessing a point of sale system from home, use a secure virtual private network with multi-factor authentication.
9. Restrict Physical Access to Cardholder Data
Physical security is often overlooked but is vital for protecting card information. Keep payment terminals and any printed receipts in secure areas. Restrict office and server room access to authorized personnel. Use locks on cabinets and doors, and maintain visitor logs. If your business accepts mail order forms or other physical documents with card numbers, store them in locked containers and destroy them securely after they are processed. Do not leave credit card information visible on counters or desks. Closed circuit cameras can deter theft and provide a record if something goes wrong.
10. Log and Monitor All Access to Systems
To detect and respond to incidents, you need to know who accessed the system and when. Turn on logging for all devices that handle card data and monitor the logs regularly. Use centralized logging tools or security information and event management systems if possible. Even small businesses can benefit from simple logging by enabling audit trails on payment software and checking them for unusual activity. If a breach occurs, logs are often the only way to understand what happened and how to respond. Retain logs for at least a year as required by the standard and protect them from alteration.
11. Test Security Systems and Processes Regularly
Many breaches occur because a vulnerability went unnoticed. Regular testing helps catch problems before attackers can exploit them. Conduct vulnerability scans on your networks and systems at least quarterly and after any significant change. Use both automated tools and manual review. Penetration testing by a qualified assessor can simulate an attacker and reveal weaknesses in network segmentation and access controls. Small businesses that use payment processors and do not store card data may have simpler testing requirements, but it is still important to test web applications and point of sale systems to ensure they are properly configured and patched. Document test results and track remediation efforts.
12. Maintain a Comprehensive Information Security Policy
A policy provides a foundation for consistent behavior and shows that management supports security efforts. The policy should cover all aspects of handling cardholder data, from network security and physical controls to employee training and incident response. Review and update the policy at least once per year to reflect changes in the business or the regulatory environment. Provide training to all employees on the policy and document their acknowledgment. Include guidelines for using third-party service providers and ensure that contracts require them to be compliant. When new staff join, include security policy training as part of the onboarding process.
Understanding PCI Compliance Levels for Small Businesses
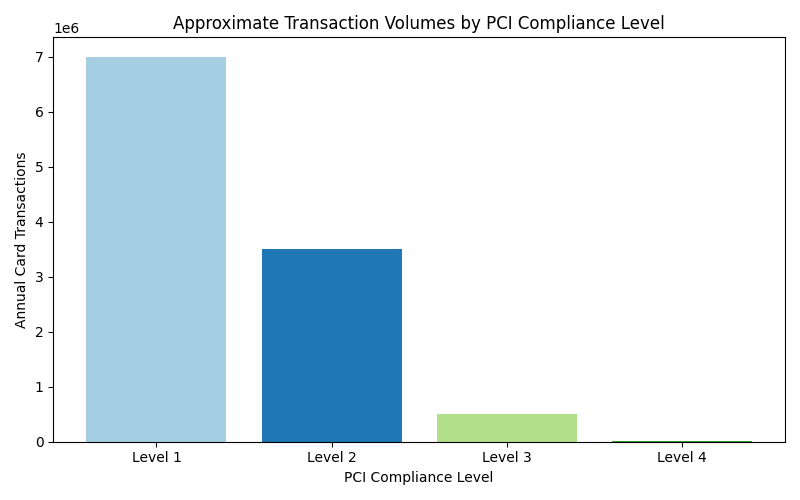
PCI DSS defines four levels of compliance based on the volume of card transactions processed each year. The level determines whether a business needs a formal audit by a Qualified Security Assessor or can complete a self-assessment questionnaire.
- Level One applies to businesses that process more than six million card transactions annually and requires a yearly on-site assessment by a qualified assessor.
- Level Two covers those processing between one and six million transactions and may require quarterly scans and a self-assessment.
- Level Three is for merchants processing between twenty thousand and one million transactions and involves completing a self-assessment questionnaire and quarterly scans.
- Level Four applies to businesses processing fewer than twenty thousand e-commerce transactions or up to one million non-e-commerce transactions.
Most small retailers and restaurants fall into Level Three or Level Four. Understanding your level helps you know which forms to fill out and what validation is required.
Practical Steps to Maintain Compliance
Meeting the twelve requirements may seem daunting, but small businesses can simplify compliance by focusing on practical steps. Below are recommendations that cover both technology and process.
1. Use a Reliable Payment Processor
One of the easiest ways to reduce the scope of PCI compliance is to use a third-party payment processor or gateway that handles card data for you. When customers pay online, the card details are entered into the processor’s hosted form rather than your website. For point of sale terminals, consider devices that encrypt data at the moment of entry and send it directly to the processor. This design, sometimes called point-to-point encryption, keeps card numbers out of your network. Choose a processor that is certified as PCI compliant and ask for an Attestation of Compliance. Even when using a processor, you still need to ensure that your network, devices, and policies meet the relevant requirements, but the workload is much smaller.
2. Complete the Appropriate Self Assessment Questionnaire
The PCI Security Standards Council publishes Self Assessment Questionnaires tailored to different merchant types and payment channels. Each questionnaire corresponds to a category such as retail, mail order telephone order, e-commerce or purely hosted solutions. For example, SAQ A applies to merchants that outsource all card processing and have no electronic storage of card data. SAQ C covers merchants with payment application systems connected to the internet. Review the descriptions of each questionnaire and complete the one that matches how you process payments. The questionnaire guides you through the requirements that apply to your environment and records your attestation of compliance. Keep a copy on file and provide it to your acquiring bank or processor when requested.
3. Document Your Processes and Train Staff
Clear documentation makes it easier to maintain compliance and to show auditors that you follow procedures. Document how devices are configured, how access is granted and revoked, how incidents are handled and how backups are performed. Write simple instructions for employees on how to handle card data, what to do if they suspect a breach, and how to report suspicious activity. Training should be conducted regularly and should include all staff who handle card information. Awareness helps prevent social engineering attacks and ensures that everyone understands the importance of security.
4. Monitor Vendors and Service Providers
Many small businesses rely on outside vendors for web hosting, payment processing, accounting, and other services. Ensure that each vendor understands and meets PCI requirements. Review their compliance reports and ask for proof of certification. Contracts should require them to maintain compliance and to notify you of any breaches. Do not assume that using a third party relieves you of all responsibility; you must still ensure that your own processes are secure and that vendors are properly vetted.
5. Keep Software and Devices Updated
Small businesses often delay updates due to fear of downtime. However, running outdated software creates security risks. Set a regular schedule for applying updates to operating systems, point of sale software, and e-commerce platforms. When possible, enable automatic updates to ensure timely patching. If you are unsure about an update, test it on a non-production device first. Keep an inventory of all devices and software to ensure nothing is overlooked. When a device reaches the end of its support life, plan to replace it.
6. Segment Your Network
Not all devices need to communicate with payment systems. Segmenting your network separates sensitive systems from less sensitive ones. For example, create a separate Wi-Fi network for customers and guests so that their devices cannot access your point of sale or accounting systems. Similarly, keep office computers that access financial information on a different segment from media players or internet browsing devices. This reduces exposure if one segment becomes compromised and makes it easier to monitor and manage traffic.
7. Prepare for Incidents
Despite best efforts, incidents may still occur. Develop a simple incident response plan that outlines what to do if you suspect a breach. The plan should include steps for containing the issue, preserving evidence, notifying your payment processor and bank, and communicating with customers if necessary. Identify who is responsible for each action and test the plan occasionally.
Common Misconceptions About PCI Compliance
Misunderstandings about PCI compliance can lead to gaps in security. One common myth is that small businesses do not need to worry because they process a low volume of transactions. In reality, breaches can happen to businesses of any size, and smaller merchants may be targeted because attackers expect weaker security. Another myth is that using a secure processor eliminates all obligations. While using a processor reduces scope, you still need to manage your network, keep devices updated, and train staff. Some believe that completing a questionnaire once is enough, but compliance is an ongoing process that involves continuous monitoring and improvement. Finally, many think that passing a scan means the environment is secure. Scans are snapshots in time and may not catch everything. Ongoing vigilance is essential.
Final Thoughts
Making Compliance Part of Your Business Culture
PCI DSS compliance is an ongoing part of running a business that accepts card payments. By understanding the requirements, using secure service providers, applying best practices, and training staff, small businesses can protect their customers and themselves from data breaches and financial loss. The cost of noncompliance includes fines, reputational damage, and loss of customer trust. Demonstrating a strong commitment to security can build confidence and set your business apart. Keeping compliance in mind as you grow ensures security scales with sales, allowing you to build a secure payment environment and focus on serving customers with peace of mind.